I was writing Go applications since 2016 and I was able to go thru various dependencies management systems including famous at some point DEP and now built-in go modules. While go dependency management came long road in language history it still has one major flaw – all dependencies are downloaded from Internet, mostly from github nowdays and there is no guarantee, except watchful eye of communities, that those deps are secure.
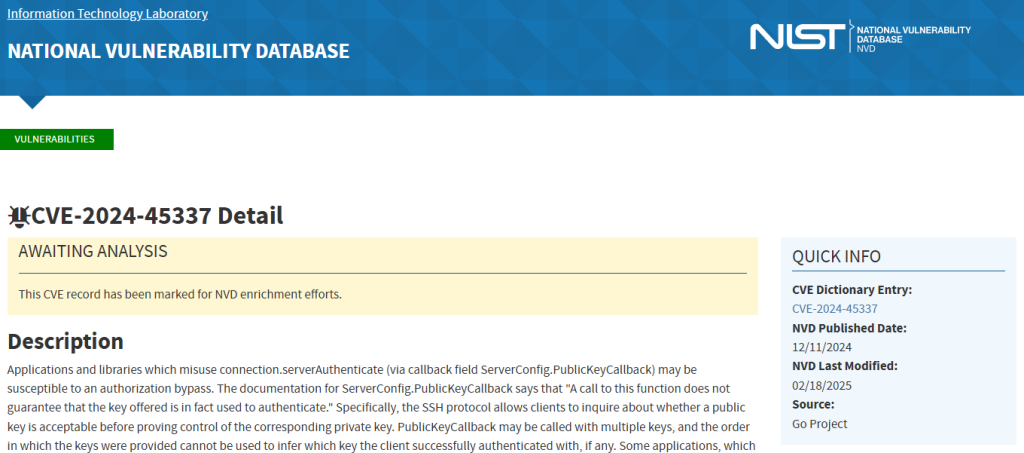
That made me thinking – we’re putting so much effort into security and development of CISO compliance applications but we still don’t know what libraries we do include in our Golang apps are doing.
It’s not only Golang problem to be fair – same issue persists in Python, Node.JS and Javascript (and many more). We just assume that community will deal with it if it’s unsafe. As Node.JS history many times shown this approach to be invalid. Couple notable examples are:
1. In November 2018, the widely used event-stream package was compromised when a malicious dependency, flatmap-stream, was added. This hidden payload targeted specific applications to steal Bitcoin wallets. The attack went unnoticed for weeks, highlighting the risks of transitive dependencies. Source: https://www.theregister.com/2018/11/26/npm_repo_bitcoin_stealer/
2. Security researcher Alex Birsan demonstrated “dependency confusion” attacks by publishing malicious packages to public registries with names matching internal packages used by major companies. Due to misconfigurations, systems would fetch these malicious packages instead of the intended internal ones, leading to potential data exfiltration. Source: https://snyk.io/blog/detect-prevent-dependency-confusion-attacks-npm-supply-chain-security
3.In January 2022, the maintainer of the popular colors and faker packages intentionally introduced breaking changes. colors was updated to print gibberish in an infinite loop, and faker was wiped and replaced with a protest message. This act of “protestware” disrupted numerous applications relying on these packages. Source: https://www.bleepingcomputer.com/news/security/dev-corrupts-npm-libs-colors-and-faker-breaking-thousands-of-apps/
4. In March 2022, the maintainer of the node-ipc package introduced a dependency called peacenotwar, which, on systems with Russian or Belarusian IP addresses, would overwrite files with a heart emoji and leave a protest message. This affected projects like Vue.js that depended on node-ipc. Source: https://www.bleepingcomputer.com/news/security/big-sabotage-famous-npm-package-deletes-files-to-protest-ukraine-war/
5. In May 2023, several npm packages, including bignum, were found to be compromised through hijacked Amazon S3 buckets. Attackers exploited the node-gyp tool to inject malicious code, leading to credential theft and other security breaches. Source: https://github.com/nodejs/node-gyp/issues/1439
6.In January 2025, Cycode reported the discovery of three malicious npm packages designed to exfiltrate data or execute unauthorized actions. These packages were crafted to evade detection, emphasizing the need for vigilant dependency management. Source: https://cycode.com/blog/malicious-code-hidden-in-npm-packages
With the increasing reliance on dependencies downloaded from the internet, I knew it was just a matter of time before our applications were compromised. I realized that manually scanning Go modules for security vulnerabilities was not only tedious but also error-prone. Post-compilation makes sense in CI/CD, but can we protect our apps easily on dev envrionment, before we even include this dependency in source code? Can we automatize it?
I’ve been already using LMStudio for some time to test various AI models. We’re all on AI hype so why not to use LLM to validate those modules by it. It can “understand” source code and explain what it does so why not to use it to detect potential problems? Will it be error prone? Sure, as all LLMs can make mistakes, but it can flag and I can check one or two incidents instead of looking at whole package file by file.
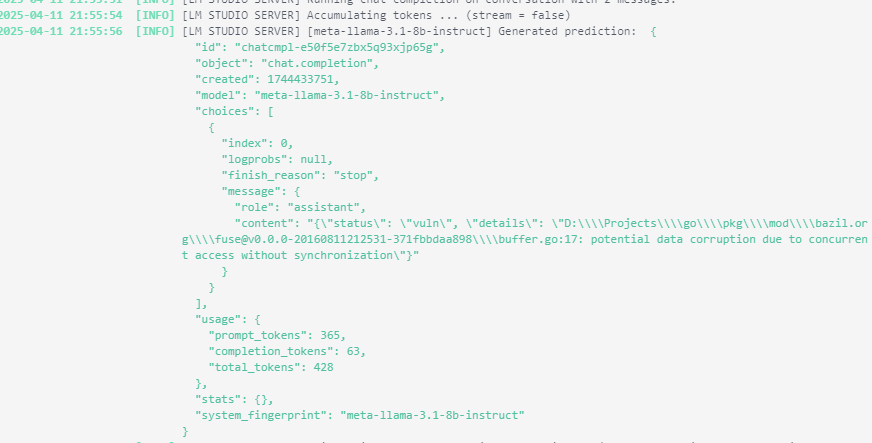
I can tell you, the performance of this tool is not great! I’ve run LMStudio on my trusty RTX 3060 GPU, and it can scan codebase in matter of minutes, but to speed things up I did added FSNotify module to my scanning app and now it does scanning of files changed in Go modules directory under GOPATH.
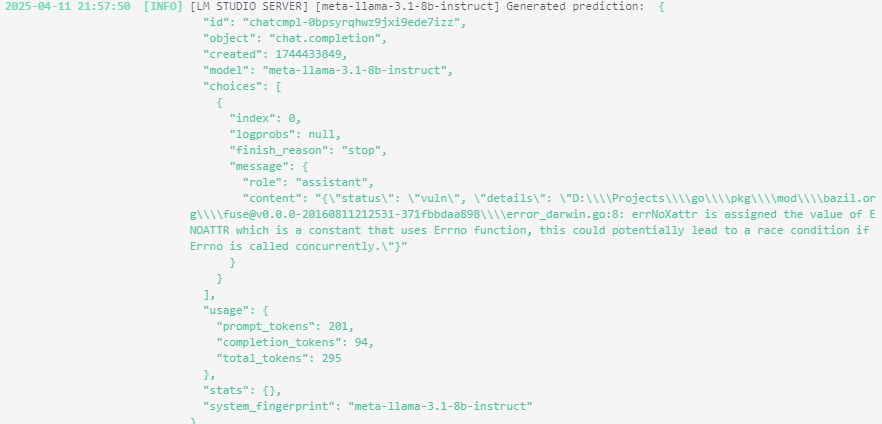
My scanning tool is not another antivirus that uses heuristic to detect threats on built software —this tool uses LLMs to understand what your code does and what security risks are imported from outside code.
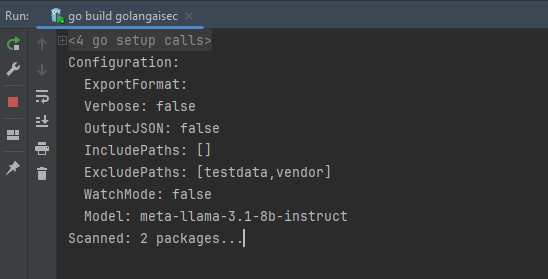
You can try it by pulling source code from here and building it on your machine: https://github.com/mateuszmierzwinski/lmstudio-example (MIT license)
It depends on my LMStudio API binding that is available here: https://github.com/mateuszmierzwinski/lmstudio (MIT license)
You can play with both or you can use second library to use LLM in your Golang projects.